by Noah Dunker
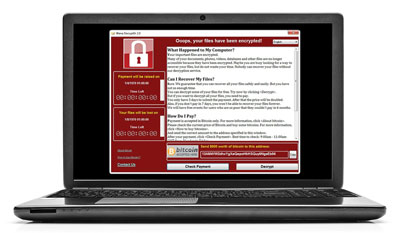
A new variant of the WannaCry ransomware family, “WanaCrypt0r 2.0,” was discovered in the wild sometime around 8:00 AM GMT, Friday, May 12, 2017. This “worm” variant of WannaCry spreads by using a recently-fixed critical-severity Microsoft vulnerability, MS17-010, which some enterprises may not have patched yet. ThreatSweep will detect the indicators of the MS17-010 attack being used to spread, and send a HotAlert. We are actively monitoring our entire ThreatSweep customer base for any signs of WanaCrypt0r 2.0.
WanaCrypt0r has a very high risk of horizontal spread, infecting many servers and workstations within enterprises who have not applied all current Windows Updates. It is using a similar technique to spread over the Internet, but is also likely relying on spam, and tricking users into running email attachments to get the initial infection inside organizations. This wave of infections has already shut down several companies, including ISPs and hospitals in Europe. It is likely to spread through the US as business continues today.
As with most malware, infected systems should be quarantined from the network immediately, and it may be prudent to segregate uninfected systems as well until the spread vector has been mitigated. The most reliable way to recover from any ransomware attack is by formatting and reinstalling infected systems, then restoring critical files from backups once the infection has been cleared.
Note that over the weekend, Microsoft also released patches for certain unsupported platforms such as Windows XP and Windows Server 2003.
Action items to reduce risk:
• Implement a progressive patching and software update policy. A fully-patched Windows system is not vulnerable to the worm component of this ransomware campaign.
• Reduce exposure of unnecessary network services (RDP, SMB, Etc), especially to the Internet, but internally where possible. Workstations should not usually have SMB file sharing enabled.
• Check that critical files are being backed up, both on-site and off-site. Frequent testing of backup recovery keeps IT staff confident in the validity of these backups and in the steps required to restore operations from it.
• Disconnect potentially infected systems as quickly as possible.